In the previous article we learned about the basic concepts behind Azure networking. In this article we will dive deep into the services used to create a modern network that can handle high amounts of traffic.
One of the benefits of cloud infrastructure is that resources can easily scale to demand. Modern networks need to be able to scale and adapt to unpredictable changes in size and growth. Fortunately, Azure offers many services to create a scalable virtual network.
VPN Gateways
- Connect on-premises networks to Azure virtual networks through a site-to-site connection.
- Connect individual devices to Azure virtual networks through a point-to-site connection.
VPNs are used to securely connect on-site networks to Azure networks.
Peering is used to connect Azure networks to other Azure networks.
VPNs connect multiple networks together, but they have a max bandwidth of 10 Gbps, a higher latency, and cost than peering. Peering is also done privately over the Azure network. When virtual networks are connected through both a VPN gateway and virtual network peering, traffic flows through the peering configuration.
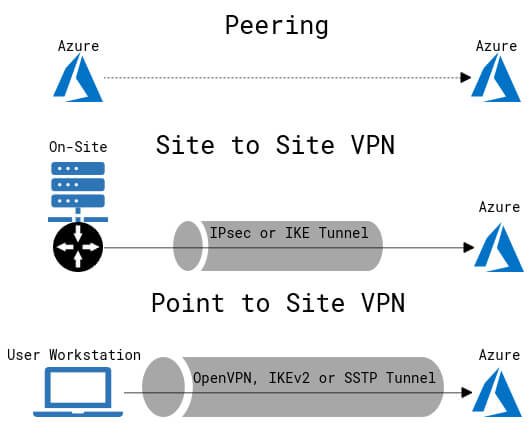
VPN Gateway Types:
- Site-to-site Virtual Private Networks: connects an on-site VPN device or gateway to an Azure virtual network with an Azure VPN gateway. An ASCII string secret is used to authenticate between the VPN device and the VPN gateway.
- Uses IPsec or IKE protocols
- Point-to-site Virtual Private Networks: connects individual client computers to Azure services, uses Azure Active Directory or Azure certificates to initiate an encrypted VPN connection.
- Uses OpenVPN, IKEv2 or SSTP protocols
In order for a VPN connection to be created, an Azure virtual network must have a virtual network gateway (VPN gateway) to send and receive data.
Azure virtual network gateways are an endpoint for encrypted connections from on-prem to Azure or between Azure virtual networks. This is the virtual network’s interface for inbound and outbound traffic.
The Azure virtual network must also have a subnet named GatewaySubnet for the gateway services.
- It must have this name for the gateway to work, and it should not contain any other resources.
- Use at least a /27 address mask to make sure you have enough IP addresses in the subnet for future growth
QUICK START
- Determine the address spaces to be used by all of your connecting networks.
- Create an Azure virtual network. Create the subnet named GatewaySubnet.
- Create a VPN gateway for the virtual network. Add it to GatewaySubnet. Create a new public address for site-to-site VPNs.
- Site-to-site VPNs: Create a local network gateway with your on-site VPN device’s public IP address and configure the VPN device. You may be able to download a script from the portal in All Services, Networking, and selecting the connection. Point-to-site VPNs: generate a client certificate, upload it to Azure, and configure the local client.
- Set address pool: Set-AzVirtualNetworkGateway
- Generate client certificate: New-SelfSignedCertificate
- Export certificate public key
- Upload cert to Azure Add-AzVpnClientRootCertificate
- Configure local client New-AzVpnClientConfiguration
Policy-based VPNs use static IP addresses for legacy VPN devices that can only use IKEv1. Routing/forwarding tables direct traffic with routes that are static.
Route-based VPNs use dynamic routing or IP forwarding tables to decide which tunnel interfaces to send each packet. Route-based VPNs are preferred because they are dynamic and more resilient to changes in the network.
VPN SKUs: VPNs are offered in various sizes that provide different levels of bandwidth, max tunnels, and pricing. The Basic VPN provides a maximum of 10 tunnels with a 100 Mbps bandwidth.
Active/active: With BGP you can have two active VPN gateways with two public addresses that are always active to mitigate outages.
Load Balancers
Azure Load Balancer: distributes network connections across multiple virtual machines or other services within the same region.
Distributing connections across multiple machines increases the resiliency of the system by removing single points of failure.
Azure Load Balancer uses the IP address to route the request to the appropriate resource on OSI Layer 4 (the transport layer).
By default it uses a 5-tuple hash-based algorithm to distribute traffic:
- Source IP
- Source port
- Destination IP
- Destination port
- Protocol type
Stateless: clients might be directed to a different virtual machine for each session since source port changes each time.
To connect the client to the same virtual machine each session, you will need session persistence. Use Source IP affinity mode for 2-tuple hashes: source IP and destination IP to always connect the client to the same VM, or 3-tuple hashes: source IP, destination IP, and protocol to connect the client depending on the service requested.
Health Probes can be used to monitor the health of the virtual machines in the backend pool.
Availability set: Allows a load balancer to distribute work among a group of virtual machines with similar functions that are hosted across different racks within the same data center to mitigate hardware failure.
Availability zone: Allows a load balancer to distribute work amoung a group of virtual machines with similar functions that are hosted across different data centers within the same geographic region to mitigate location failure.
Internal load balancers: balances traffic from internal networks within Azure. Must assign the load balancer a private address and place the load balancer in the same private network as the VMs.
External load balancer: balances traffic from the internet with public addresses.
Azure Application Gateway
Application gateways use the URL of the request to route traffic. If a client requests a URL ending in /images, they can be directed to a pool of servers separate from a URL ending in /videos. Application gateway routes the requests to the appropriate web server according to a set of rules.
- Supports the HTTP, HTTPS, HTTP/2 and WebSocket protocols.
- Enable web application firewall to protect against web application vulnerabilities.
- End-to-end request encryption.
- Autoscaling, to dynamically adjust capacity as your web traffic load changes.
Additionally, it can also be used for:
- Redirection: redirect one site to another
- Rewrite HTTP headers: pass additional information in the headers between client and server
- Custom error pages: display a custom page when user encounters a web error
- Web application firewalls to protect against web application vulnerabilities.
VPN gateways, Load Balancers, and Application Gateways
A common question is what is the difference between VPN gateways, load balancers, and application gateways.
While VPN gateways operate on the network (OSI layer 3 primarily), load balancers operate on the transport layer (OSI layer 4) by using the IP address to route traffic, and application gateways operate on the application layer (OSI layer 7).
Azure Traffic Manager
Azure Traffic Manager is a DNS-based global load balancer used to improve the performance and availability of your application.
- Distribute traffic from users across region backends
- It can route any protocol, not just HTTP traffic.
- It cannot filter based on HTTP properties or do TLS termination since it is DNS based. Use Azure Front Door for this.
- Uses endpoint monitoring to monitor health of application.
Azure Front Door
Azure Front Door is a Layer 7 (HTTP/HTTPS application layer) global load balancer similar to Application Gateway but for global services.
- Can route traffic based on HTTP properties such as browser’s country code and TLS protocol termination.
- Only routes HTTP/HTTPS traffic, no other protocols.
- Can assign priorities to various endpoints to direct traffic.
- Can implement health probes to monitor endpoints.
Azure CLI VPN Cheatsheet
Create the GatewaySubnet and add it to a virtual network:
az network vnet subnet create \
--resource-group [resource group name] \
--vnet-name [VNet_Name] \
--address-prefix [10.0.255.0/27] \
--name GatewaySubnetCreate the virtual network gateway:
az network vnet-gateway create \
--resource-group [resource group name] \
--name [Vnet_Gateway_Name] \
--public-ip-address [PIP_Name] \
--vnet [Vnet_Name] \
--gateway-type Vpn \
--vpn-type RouteBased \
--sku VpnGw1 \
--no-waitView the public IP address:
az network public-ip show \
-g [resource group name] \
--name [PIP_Name]Create the local network gateway:
az network local-gateway create \
--resource-group [resource group name] \
--gateway-ip-address [Vnet Gateway PIP] \
--name [Local_Gateway_Name] \
--local-address-prefixes [On-prem IP address space]Show the virtual network gateway status:
az network vnet-gateway list \
-g [resource group name] \
-o tableShow the local network gateway status:
az network local-gateway list \
-g [sandbox resource group name] \
-o tableTo update the local network gateway IP address:
az network local-gateway updateCreate the VPN connection:
az network vpn-connection create \
--resource-group [resource group name] \
--name [VPN Name] \
--vnet-gateway1 [Vnet_Gateway_Name] \
--shared-key [IPSec pre-shared key] \
--local-gateway2 [Local_Gateway_Name]Show the VPN connection status:
az network vpn-connection showCreate an application gateway:
az network application-gateway createCreate a load balancer:
az network lb create \
--resource-group [resource group name] \
--name [Load_Balancer_Name] \
--public-ip-address [PIP_Name] \
--frontend-ip-name [Frontend_Pool_Name] \
--backend-pool-name [Backend_Pool_Name]View a load balancer’s front end IP address:
az network lb frontend-ip list
-g YourResourceGroup \
--lb-name [Load_Balancer_Name] \
--query
"[].{Name:name,PublicIpName:publicIpAddress.id}" \
-o tableCreate a health probe monitoring port 80 on the load balancer:
az network lb probe create \
--resource-group [resource group name] \
--lb-name [Load_Balancer_Name] \
--name [Health_Probe_Name] \
--protocol tcp \
--port 80 View a load balancer’s heath probes:
az network lb probe list
-g [resource group name] \
--lb-name [Load_Balancer_Name] \
-o tableCreate a rule for the load balancer:
az network lb rule create
--resource-group [resource group name] \
--lb-name [Load_Balancer_Name] \
--name [Rule_Name] \
--protocol tcp \
--frontend-port 80 \
--backend-port 80 \
--frontend-ip-name [Frontend_Pool_Name] \
--backend-pool-name [Backend_Pool_Name] \
--probe-name [Health_Probe_Name]View a load balancer’s rules:
az network lb rule list
-g [resource group name] \
--lb-name [Load_Balancer_Name] \
-o tableUpdate a virtual machine’s NIC to use the load balancer:
az network nic ip-config update \
--resource-group [resource group name] \
--nic-name [NIC_Name] \
--name [ipconfig_Name] \
--lb-name [Load_Balancer_Name] \
--lb-address-pools [Backend_Pool_Name]Official Azure VPN Gateway documentation.
Now that we know about some of the tools used to scale networks out, we can dive deep into common network designs for enterprise environments.
