When designing a modern network, the engineer must account for failure. There are four main pillars of design that make for great architecture.
- Availability
- Scalability
- Reliability
- Security
Availability: The system must be highly available so that it can be accessed by users all times of the day.
Scalability: The system must be performant and adaptable to unpredictable changes in demand.
Reliability: The system must be maintainable and resilient to failure.
Security: The system needs to be defensive and protected from unauthorized access.
There are various strategies to address each one of these factors, below we will explore common architectures of Azure networks.
Azure Virtual WAN
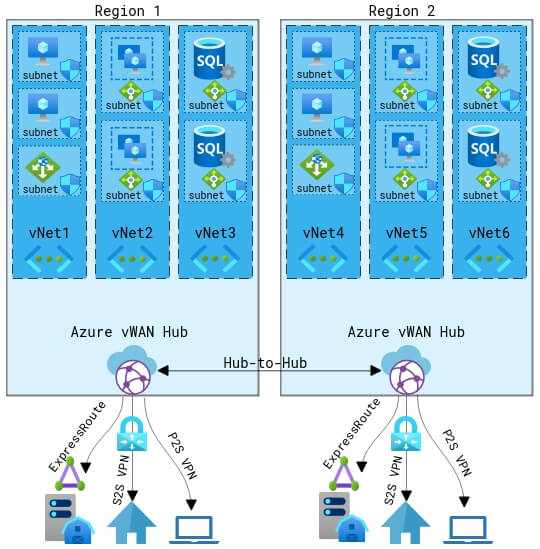
Azure’s most robust offering for large global networks is Azure Virtual WAN.
As opposed to using traditional site-to-site VPNs, which are limited to a maximum of 30 concurrent tunnels, Azure vWAN expands that to a limit of 2,000 tunnels and can greatly minimize the latency of global connections.
Azure Virtual WAN is a Software Defined WAN (SD-WAN) that increases the scalability and reliability of the network by reducing the need to manage multiple VPNs, VNAs, and NSGs across several regions.
Azure Virtual WAN currently has an SLA of 99.95% availability.
It works exceptionally well with large complex networks but can be very costly as opposed to the traditional hub and spoke network topology.
Hub and Spoke
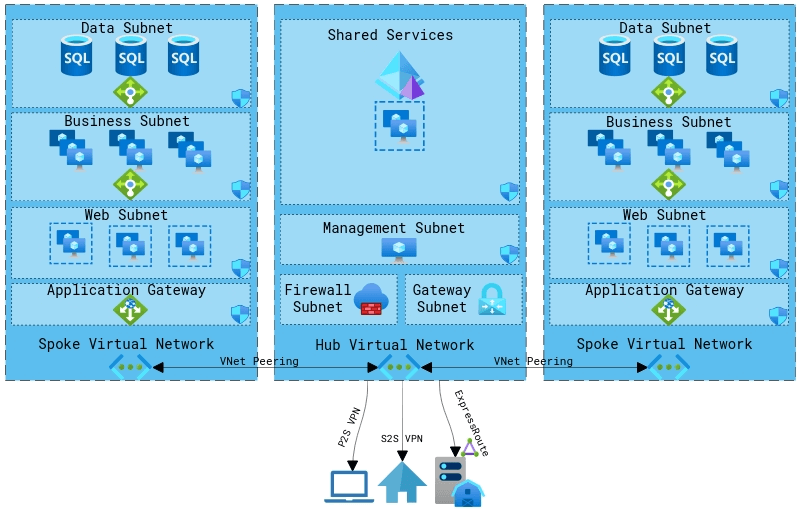
The hub and spoke model is the most widely used and supported network architecture for cloud environments.
This architecture is designed with scalability and security in mind. A central hub is responsible for incoming connections and shared services. This centralized network zone allows global control over security access and management of resources shared to spoke networks.
Spoke networks are separated nodes that are linked to the hub through virtual network peering. These spoke networks are responsible for the majority of production on the network.
Each spoke can have workloads segregated from each other that can be added or removed as demand fluctuates. Spokes can be easily added and connected to the hub as business grows or workloads change.
Each spoke network is further segregated into an n-tier architecture.
N-tier Architecture
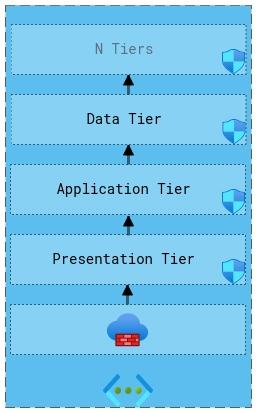
N-tier architecture is a separation of services into individual layers to further increase the security and resiliency of the network.
Services are logically separated by their role into separated tiers and then physically segregated into subnets which enforce network security groups on the traffic. Tiers can be restricted to traffic only from the tier immediately below it or open to all tiers below it.
Although the diagram above shows 3 tiers (presentation, application, and data) an endless amount of tiers can be created for each role that exists, which is why it is named the n-tier architecture.
Microservices
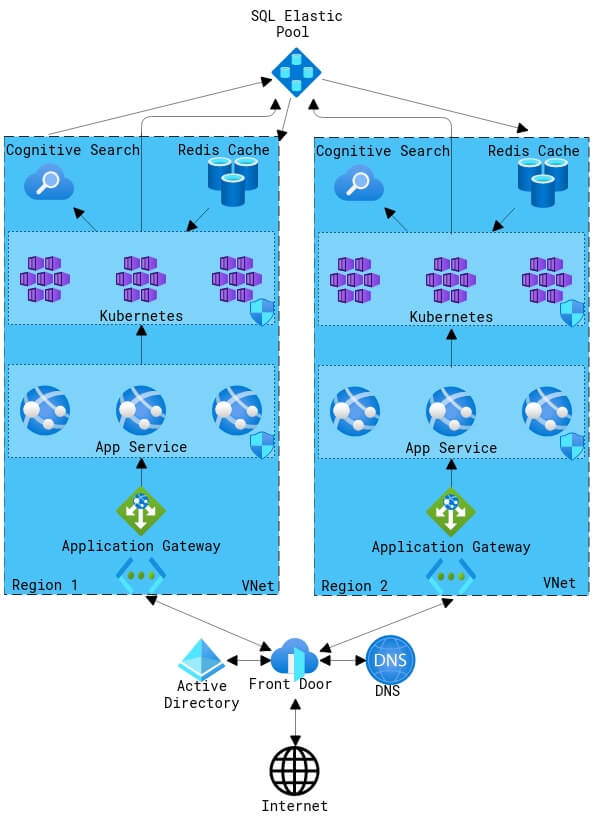
Another type of architectural design that is quickly gaining traction is microservices architecture.
Services are traditionally coupled together in order to make them easier to manage and secure, but what often happens is the host becomes an overbearing monolith that contains “all eggs in one basket.” The host becomes a single point of failure that is difficult to scale and difficult to diagnose.
By decoupling the services into smaller “microservices” on independent hosts, the scalability and availability are drastically increased.
Managing these independent hosts would normally be extremely cumbersome, but with fully managed services such as Azure App Service and Azure Kubernetes much of the overhead is removed.
Learn more about Azure network topologies from the official documentation here.
If you liked these network diagrams, create one here.
