Azure virtual networks provide the key capabilities for resources to communicate with each other:
- Communicate between Azure resources
- Communicate with on-premises resources
- Internet connectivity
- Isolation and segmentation
- Filter network traffic
- Route network traffic
- Connect multiple virtual networks
A virtual network is composed of many different components including, but not limited to, network interfaces, load balancers, subnets, network security groups, and public IP addresses.
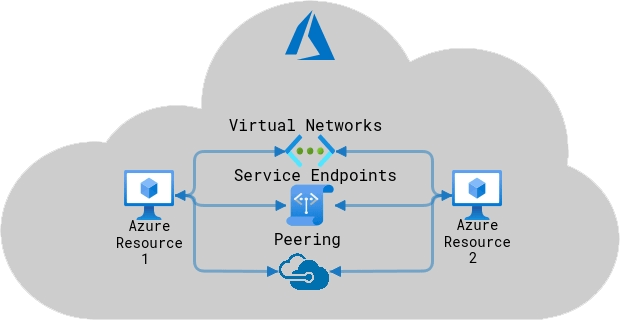
Three ways for Azure resources to communicate between each other:
- Virtual networks: resources in the same virtual network can communicate with each other
- Service endpoints: direct connection to services through private addresses so that they can’t be intercepted over internet
- VNet peering: resources in separate regions can be configured to communicate with each other over private addresses
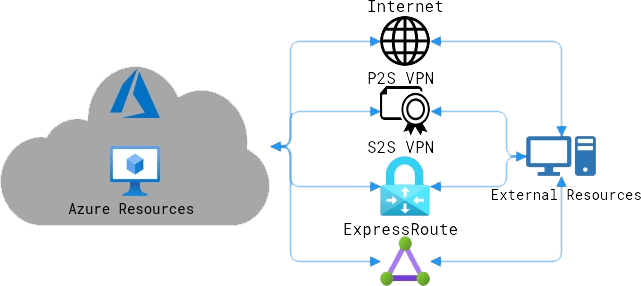
Four ways for Azure resources to communicate with external resources:
- Over the internet (unsecure): data can be communicated over the public internet.
- Point to site virtual private networks (VPN): computers individually configured to securely communicate to Azure networks. Best for remote workers.
- Site to site VPNs: an on-site VPN gateway device connects an entire on-site network to Azure networks on an encrypted connection over the internet.
- Azure ExpressRoute: direct private connection to Azure through an ExpressRoute partner that doesn’t touch public internet.
By default, all Azure resources within a virtual network are able to connect to the internet. For external resources to send data into the Azure network, they must send the data to a public facing endpoint (a public IP address). All resources internal to the network use private endpoints to communicate with each other.
Network interfaces (NIC): an interface that connects virtual machines to the network. Each VM has at least one network interface, these provide IP address connectivity to the machine and send/receive data from the network. Adding or removing NICs requires shutting the VM down.
Azure virtual network gateway: an endpoint for encrypted connections between two separate networks, either virtual or external networks. These are the interfaces for one network to communicate with another network. A virtual network can only have one gateway assigned (except connecting ExpressRoute and VPN gateways).
QUICK START
In the Azure portal, create a virtual network by selecting Create a resource and selecting Create a virtual network or by typing virtual networks in the search bar.
When you set up a virtual network, you define a private IP address space, using either public or private IP address ranges. You can then segment that IP address space into subnets, and allocate part of the defined address space to each defined subnet.
IP Addresses
The “telephone numbers” of computer networks that allow other computers to communicate with each other.
Public Addresses: IP addresses that connect directly to the internet, used for public-facing services. You cannot choose a public address in Azure, it is automatically picked from a pool depending on its region.
Private Addresses: internal IP addresses that are used to connect within a network. Addresses are assigned by DHCP. Private addresses must be in this range (RFC1918):
- 10.0.0.0 to 10.255.255.255 (/8)
- 172.16.0.0 to 172.31.255.255 (/12)
- 192.168.0.1 to 192.168.255.255 (/16)
CIDR (classless inter-domain routing) is a shorthand notation for a block of adjacent IP addresses.
/8 notates a block of 16,777,216 addresses (10.0.0.0 – 10.255.255.255)
/12 notates a block of 1,048,576 addresses (10.0.0.0 – 10. 15.255.255)
/16 notates a block of 65,536 addresses (10.0.0.0 – 10.0.255.255)
/22 notates a block of 1,024 addresses (10.0.0.0 – 10.0.3.255)
/23 notates a block of 512 addresses (10.0.0.0 – 10.0.1.255)
/24 notates a block of 256 addresses (10.0.0.0 – 10.0.0.255)
Azure reserves 5 addresses in a subnet, the first four address and the last. (For example, in a /24 subnet: .0, .1, .2, .3, .255 are reserved)
Total available addresses in a subnet: 2^(32-n)-5 where n is the CIDR notation.
Each public or private address can be Dynamic or Static.
Dynamic: The address is temporary and changes often, when the VM powers off or the DHCP lease is up.
Static: IP address will stay the same for the lifetime of the product, even if it powers down.
IP address SKUs:
Basic: Non-redundant addresses that can be assigned to most resources and are open to incoming traffic by default.
Standard: zone-redundant addresses best suited for VPNs, Load Balancers, application gateways, and network interfaces, closed by default.
Azure will close a connection if traffic ceases for 4 minutes by default.
Subnets
Subnets allow you to segment your network into “sub networks” to provide isolation within the virtual network.
Subnet names must begin with a letter or number, end with a letter, number or underscore, and may contain only letters, numbers, underscores, periods, or hyphens. Remember, Azure reserves 5 IP addresses for every subnet (first and last for network ID, and then 3 after the first address).
Design Considerations:
- Subnets cannot overlap
An address space cannot belong to two separate subnets, the subnet wouldn’t be isolated. - IP addresses must be unique
You cannot have two hosts with the same IP address in different locations, it would be impossible to route traffic between those two hosts. - VPN gateways will require a gateway subnet called GatewaySubnet
It must have this name for the gateway to work, and it should not contain any other resources. Use at least a /27 address mask to make sure you have enough IP addresses in the subnet for future growth.
Subnets are isolated from each other even though they may be in the same virtual network. Traffic from one subnet must pass a network security group to travel to another subnet.
Network Security Groups
Network security groups filter incoming and outgoing traffic between virtual machines and subnets, including connections from virtual networks and the internet. These are the security rules enforced on subnets and network interfaces.
Connections are stateful: allowing inbound traffic on a port will allow it to respond outbound on the same port. For example, if you allow inbound traffic on port 443 (HTTPS), outbound traffic on port 443 will be allowed.
Azure Routes
Routes direct the flow of traffic between subnets, virtual networks, and on-prem networks. Route tables define where network traffic is sent.
Every subnet has these default routes that can’t be removed:
Traffic leaving a subnet is sent to the Next hop type when the IP address matches the address prefix.
- Virtual network: traffic goes to other address spaces of the virtual network (other subnets)
- Internet: Routes traffic to the internet, unless it’s an Azure service which will use Azure’s backbone.
- None: traffic gets dropped and stays within the subnet. These are reserved for private use RFC 1918, 6598
More routes are created when the following is enabled:
- Virtual network peering: connection between Azure networks in separate locations or regions.
- Service chaining: user defined routes from one virtual network to a virtual appliance or gateway within a peered network.
- Virtual network gateway: traffic between virtual networks or Azure and on-prem.
- Virtual network service endpoint: direct connection to Azure services with private addresses
User defined routes: Custom routes can be created for greater control over the flow of network traffic.
- Virtual appliance: Route traffic to a firewall to filter traffic, or a load balancer.
- Virtual network gateway: Route traffic to a virtual network gateway or VPN.
- Virtual network: Route traffic within a virtual network.
- Internet: Route traffic to the internet.
- None: Drop the traffic.
Border Gateway Protocol (BGP): routes traffic between different networks (such as on-prem and Azure networks).
- ExpressRoute: traffic routes directly from on-prem to Azure
- VPN site to site: connects on-prem networks to Azure over the internet
If multiple routes are available in a route table, Azure uses the route with smaller scope. For example, a message sent to the IP address 10.0.0.2, with two routes available: 10.0.0.0/16 and 10.0.0.0/24 prefixes. Azure selects the route with the 10.0.0.0/24 prefix because it’s more specific, with less addresses.
If multiple routes share the same address prefix, Azure selects the route based on its type in the following order of priority:
- User-defined routes
- BGP routes
- System routes
Network virtual appliances: virtual machines that control the flow of network traffic with IP routing. Examples: firewalls, WAN optimizers, application-delivery controllers, routers, load balances, proxies, and SD-WAN edges.
These can be used to increase the security of traffic flow between subnets.
Deploy a NVA by configuring a VM, set up the subnets, routing tables, and user define routes, then enable IP forwarding to the NVA, or use a partner image from the Azure Marketplace.
Virtual Network Peering
Traffic between Azure virtual networks can be routed through the Azure network using private addresses. It doesn’t rely on internet connectivity, gateways, or encrypted connections and offers high bandwidth, low latency.
Virtual network peering connects two networks in the same Azure region.
Global virtual network peering connects two networks in separate Azure regions.
It requires the connection to be reciprocal: both networks must be configured for pairing.
The IP address spaces of the connected networks cannot be overlapping.
To enable administration of the partner network, the administrator must have the Network Contributor role
Nontransitive: peered networks can’t network to peers of peers. In the setup A ↔ B ↔ C, A won’t be able to connect to C.
Use transitive gateways to connect multiple networks: Select Allow gateway transit to have a gateway act as a hub for multiple vnet peering
When virtual networks are connected through both a gateway and virtual network peering, traffic flows through the peering configuration.
Azure ExpressRoute
Azure ExpressRoute is a private high-bandwidth connection that connects on-premises networks directly to Azure with internet service provider partnerships and doesn’t touch the public internet.
It supports active/active connections for more reliability, increased security, minimal latency, and up to 100 Gbps bandwidth.
It uses BGP over layer 3 to provide a secure connection directly to Azure.
It requires:
- An ExpressRoute partner or cloud exchange provider that can set up your onsite connection
- An Azure subscription that is registered with your chosen ExpressRoute connectivity partner
- An active Microsoft Azure account that can be used to request an ExpressRoute circuit
- BGP sessions for routing domains have been configured
- NAT service to translate private addresses into public addresses
- Several blocks of IP addresses in your network reserved for routing traffic to the Microsoft cloud, either a /29 subnet or two /30 subnets
It is best suited for:
- Low-latency connections to cloud services
- Accessing high-volume systems in the cloud
- Consuming Microsoft Cloud Services, such as Office 365 and Dynamics 365
- Organizations with large-scale on-premises systems migrated to Azure
- High security situations where data should not traverse the public internet
Azure CLI Networking Commands
Create an Azure Virtual Network with a subnet:
az network vnet create \
--resource-group [sandbox resource group name] \
--name [Vnet_Name] \
--address-prefix [10.0.0.0/16] \
--subnet-name [Subnet_Name] \
--subnet-prefix [10.0.0.0/24]View all Azure virtual networks:
az network vnet list -g [resource group name] --output tableView subnets of an Azure virtual network:
az network vnet subnet list -g [resource group name] --vnet-name [Vnet_Name] -o tableView Azure Network Security Groups:
az network nsg list -g [resource group name] -o tableView the rules of a Network Security Group:
az network nsg rule list -g [resource group name]
--nsg-name [NSG_Name] -o tableView the routing tables:
az network route-table list -g [resource group name]
–o tableCreate a dynamic public IP address:
az network public-ip create \
--resource-group [resource group name] \
--name [PIP Name] \
--allocation-method DynamicView all the public IP addresses:
az network public-ip list -g [resource group name]Get information on a public IP address:
az network public-ip show \
--name [PIP Name] \
--resource-group [resource group name]Create an Azure network interface:
az network nic create -g [resource group name] --vnet-name [Vnet_Name] --subnet [Subnet_Name] -n [NIC_Name]Create an IP configuration for the network interface:
az network nic ip-config create -g [resource group name] -n [IP_Config_Name] --nic-name [NIC_Name] --private-ip-address [IP Address] --make-primaryChange a network interface’s private IP address:
az network nic ip-config update -g [resource group name] --nic-name [NIC_Name] -n [IP_Config_Name] --private-ip-address [IP Address]View network interfaces by internal DNS suffix:
az network nic list --query "[?dnsSettings.internalDomainNameSuffix=`{dnsSuffix}`]"Enable IP forwarding on a NIC:
az network nic update --name [NIC_Name] \
-g [sandbox resource group name] \
--ip-forwarding trueCreate a custom route:
az network route-table route create \
--route-table-name [table name] \
--resource-group [sandbox resource group name] \
--name [subnet name] \
--address-prefix [10.0.1.0/24] \
--next-hop-type VirtualAppliance \
--next-hop-ip-address [10.0.2.4]
Associate the subnet with a route table:
az network vnet subnet update \
--name [subnet name] \
--vnet-name [vnet name] \
--resource-group [resource group name] \
--route-table [table name]Configure virtual network peering:
az network vnet peering create \
--resource-group [resource group name] \
--name [name] \
--vnet-name [current vnet] \
--remote-vnet [vnet to connect to] \
--allow-vnet-accessTo learn more about networking you can access the official Azure documentation.
In the next article we will learn more about network gateways, virtual private networks (VPNs), load balancers, how they are used to connect multiple enterprise environments, and create reliable networks that can scale to demand.
